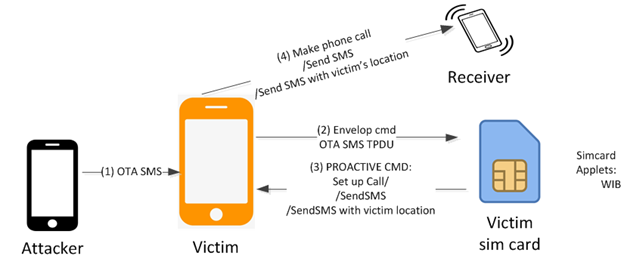
Mobile security lab, Ginno Security, has discovered a new SIM card vulnerability which uses a Wireless Internet Browser (WIB) built into a SIM card to activate over-the-air (OTA) services. The new vulnerability is called WIBattack and its exploit begins with an SMS (SMS) from the attacker’s mobile phone. The attacker sends a malicious OTA SMS containing the WIB command to the victim’s phone number. Here is a video describing WIBattack.
According to Ginno Security, once the victim receives the OTA SMS, it forwards the command to the WIB browser in the victim’s SIM card. The WIB responds to the command and sends a PROACTIVE COMMAND to the victim phone. Following the commands on the SIM card, an attacker can send a call or SMS to any phone number using the victim’s details. In addition, it can also track the user’s geographic location.
Currently, researchers have reported the WIBattack vulnerability to the GSM Association. The researchers recommend using SIMtester to test the SIM card to identify vulnerabilities in the WIB browser. In addition, they are developing SIM scanning devices that can run on Android devices.
Recall that at the beginning of this month, mobile security company, AdaptiveMobile, also found a vulnerability in SIM cards (Simjacker). According to the report, the vulnerability can work on a low-security mobile phone network provider. It also uses malicious messages to steal phone users information. With time, it gathers enough information to make calls and other activities in place of the real owner.





