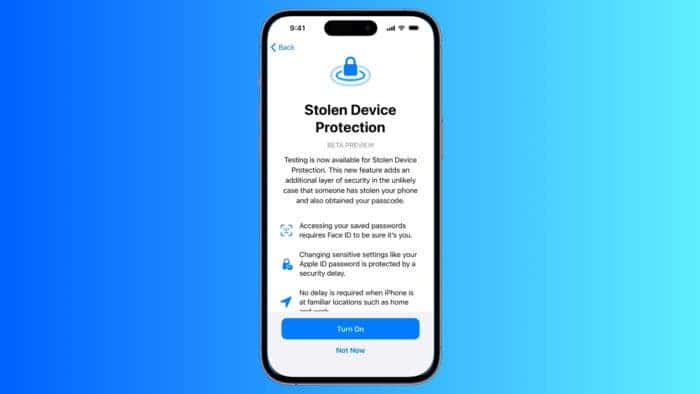
In today’s hyper-connected world, smartphones have become more than communication devices. They’re the repositories of our lives as most of us store everything in them. That includes precious memories, personal documents, and sensitive financial information. So, it goes without saying losing your phone can be stressful. Well, for iPhone users, there’s Stolen Device Protection.
At the core, Stolen Device Protection is a vital security feature introduced in the latest iOS version. It acts as a shield for your iPhone’s sensitive data. The feature throws up robust roadblocks for potential thieves. It also gives you invaluable time to react if your device ever falls into the wrong hands.
How Stolen Device Protection on iPhone Works
Imagine a thief snatching your iPhone and unlocking it with your passcode. A terrifying scenario, right? With the feature enabled, passcode wouldn’t be enough. This feature introduces two key layers of defense:
Biometric Authentication
Thieves can access your saved passwords in iCloud Keychain. They can also view your stored credit cards. But with Stolen Device Protection, there will be a biometric wall as a roadblock. It makes Face ID or Touch ID authentication mandatory for actions like:
-
Accessing synced iCloud Keychain passwords and passkeys
-
Autofilling debit and credit cards
-
Applying for an Apple Card or viewing your Apple Card number
-
Turning off Lost Mode on your iPhone
-
Erasing all content and settings
-
Transferring your Apple Cash balance

So, there will be no need to worry even if someone cracks your passcode. Your sensitive information remains shielded with Stolen Device Protection.
Security Delay
The protection feature throws another wrench in the thief’s plans. There will be a one-hour security delay for critical actions like:
-
Changing your Apple ID password or signing out
-
Changing your iPhone passcode
-
Turning Face ID or Touch ID on or off
-
Turning off Find My or Stolen Device Protection
-
Changing trusted devices, Recovery Contacts, or the Recovery Key for your Apple ID account
This time buffer buys you precious minutes to react. Imagine reporting your phone lost, activating Lost Mode to remotely lock it, and even wipe its contents. All this can happen before the thief can bypass the delay. Remember, this delay only kicks in when you’re away from familiar locations, adding an extra layer of convenience for your daily use.

How to Enable Stolen Device Protection
There’s no need to go through any intricate steps to get Stolen Device Protection turned on. You need to follow these simple steps:
-
Update your iPhone to iOS 17.3 or later. You might even see a prompt to enable the feature right after updating.
-
Ensure Face ID or Touch ID is enabled. If not, head over to Settings and follow the prompts to set it up.
Gizchina News of the week
-
Navigate to Settings > Face ID & Passcode (or Touch ID & Passcode). Enter your passcode when prompted.
-
Scroll down and tap Turn On Protection under Stolen Device Protection.
-
Authenticate using Face ID or Touch ID to complete the activation.
That’s it! You’ve successfully activated your iPhone’s built-in security shield.
Disabling Stolen Device Protection: When and How
It’s recommended to keep Stolen Device Protection active. But there might be situations where you need to disable it. Here’s how:
-
Follow the same steps as enabling, but tap Turn Off Protection instead.
-
If you’re not in a familiar location, a one-hour security delay will be triggered. Wait for the timer to run out or return to a familiar location for the delay to be lifted.
-
You’ll receive a notification prompting you to return to Settings for one final biometric check before disabling the feature.
Remember, the security delay adds valuable time to react in case your phone is lost or stolen while disabled.
Why Stolen Device Protection Matters
Think of Stolen Device Protection as an investment in your digital security. Here’s why enabling it is a no-brainer:
It adds an extra layer of security beyond your passcode
A stolen passcode only opens the door; Stolen Device Protection requires the key of your fingerprint or facial recognition for the most sensitive data.
Stolen Device Protection buys you crucial time to react
The one-hour security delay gives you a window to activate Lost Mode, wipe your device, or take other precautionary measures.
It’s hassle-free to set up and use
Enabling and using Stolen Device Protection is a straightforward process that rarely disrupts your daily iPhone experience.
Stolen Device Protection gives you peace of mind
Knowing your data is protected by an extra layer of security is a significant weight off your shoulders. You can rest assured that even if your iPhone is lost or stolen, sensitive information like passwords, financial details, and personal documents will remain inaccessible.

Beyond the Basics: Advanced Features and Tips for Protecting Your iPhone
While the core functionality of Stolen Device Protection is robust, there are extra features and tips to maximize its effectiveness:
Familiar Locations
The new protection feature learns your regular haunts based on your iPhone’s usage patterns. This ensures the security delay only activates when you’re away from trusted locations, minimizing inconvenience in your daily life.
Lost Mode
Activate Lost Mode remotely to lock your iPhone with a passcode, display a custom message, and play a sound, making it easier to locate or deter potential thieves.
Find My
Use Find My to track your iPhone’s location on a map in real-time, aiding in its recovery.
Erase All Content and Settings
As a last resort, you can erase all data from your iPhone. Do this only when there’s no hope of recovering it. This will prevent sensitive information from falling into the wrong hands.