ZecOps, a cybersecurity company, revealed a major security flaw in Apple’s native email application, leaving hundreds of millions of iPhones and iPads vulnerable. This flaw was discovered during an investigation by the company into a cyber attack which affected one of its customers at the end of 2019. It was allegedly exploited against 6 leading targets: employees of a company listed in the Fortune 500 ranking in North America, an executive from a transporter in Japan, a VIP in Germany, a journalist in Europe, a corporate executive in Switzerland and other victims in Saudi Arabia and Israel.
The vulnerability exists since the release of iOS 6 in 2012
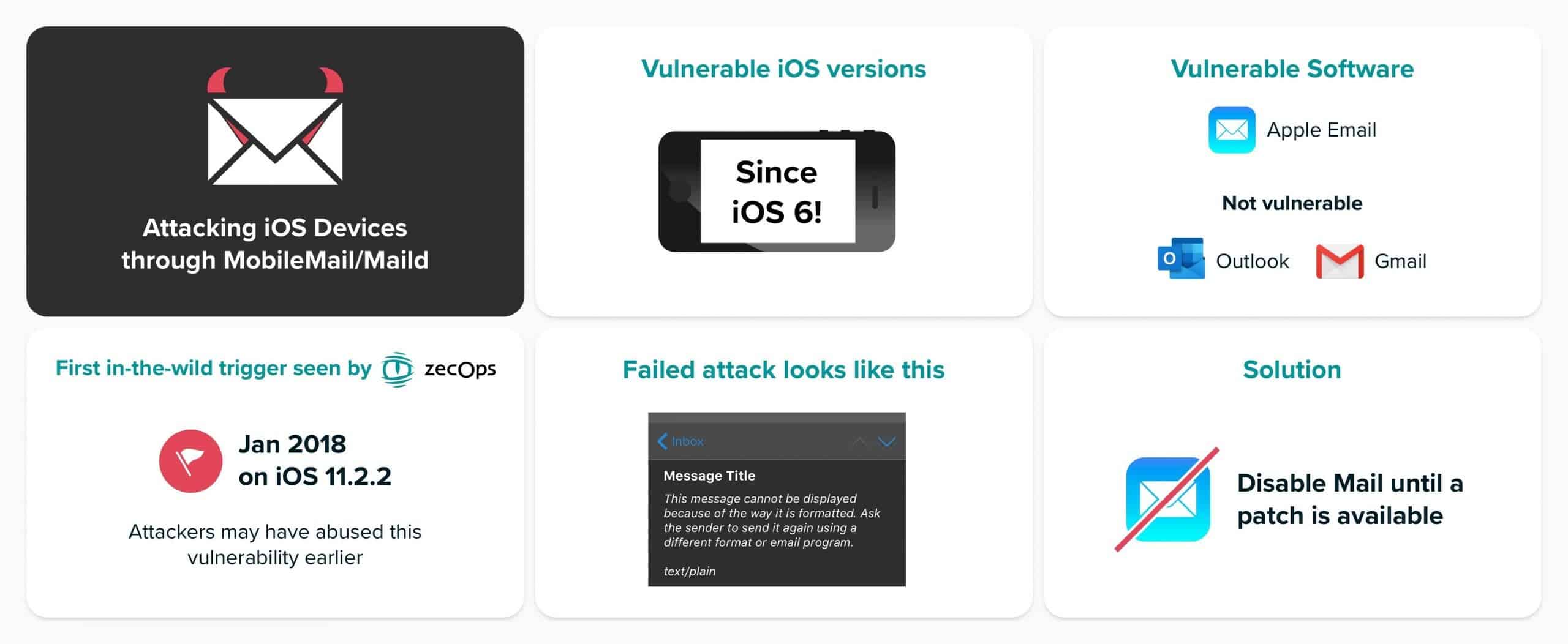
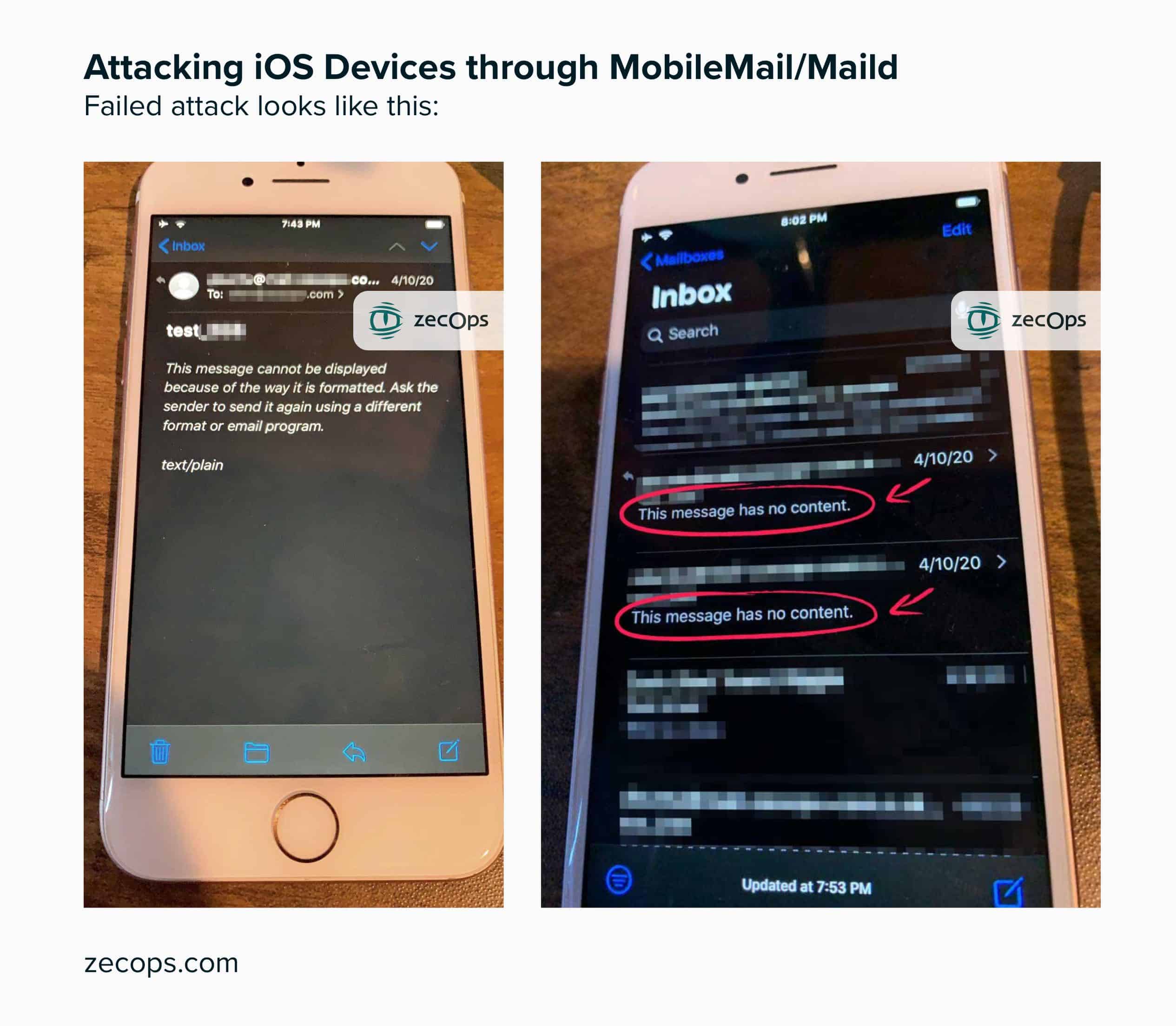
“The attack’s scope consists of sending a specially crafted email to a victim’s mailbox enabling it to trigger the vulnerability in the context of iOS MobileMail application on iOS 12 or maild on iOS 13,” explains ZecOps in its report. Exploiting this flaw, remotely, would not require any action by the victim. No file to download or corrupt site to visit. It was enough to open a blank email, at first glance, via the Mail application on mobile to force a crash and a reset. The crash thus opened the door to hackers, who could then take the data stored within the device through the application.
According to the company, a malicious program could have taken advantage of this vulnerability of the Apple mobile operating system since January 2018. Worse, according to the company, the flaw has existed in the Mail application since at least iOS 6. This was released in 2012. ” These vulnerabilities – especially remote heap overflow – are widely exploited in the wild in targeted attacks by one or more advanced threat operators,” adds ZecOps.
A patch deployed with the next iOS update
The information was taken seriously by Apple, which did not wish to comment. Contacted last March by ZecOps, the American firm acknowledged the existence of the flaw. It was corrected in the latest beta version of iOS. A patch should be deployed during the next update for all users in the coming weeks.
Impact & Key Details:
- The vulnerability allows remote code execution capabilities and enables an attacker to remotely infect a device. This is by sending emails that consume significant amount of memory
- The vulnerability does not necessarily require a large email. A regular email which is able to consume enough RAM would be sufficient. There are many ways to achieve such resource exhaustion including RTF, multi-part, and other methods
- Both vulnerabilities were triggered in-the-wild
- The vulnerability can be triggered before the entire email is downloaded
- We are not dismissing the possibility that attackers may have deleted remaining emails following a successful attack
- Vulnerability trigger on iOS 13: Unassisted (/zero-click) attacks on iOS 13 when Mail application is opened in the background
- Vulnerability trigger on iOS 12: The attack requires a click on the email. The attack will be triggered before rendering the content. The user won’t notice anything anomalous in the email itself
- Unassisted attacks on iOS 12 can be triggered (aka zero click) if the attacker controls the mail server
- The vulnerabilities exist at least since iOS 6 – (issue date: September 2012) – when iPhone 5 was released
- The earliest triggers we have observed in the wild were on iOS 11.2.2 in January 2018