You should be ashamed if you thought the digital world was safer than the real world. Not a day goes by without news of some company suffering a data breach. You can’t name a company that hasn’t had such a problem. Moreover, the biggest data leaks have happened at the big brands. We suppose you blame these companies for weak security measures. But it’s a global problem, and they (and we) are no saints. Recently we heard about a new Android banking trojan that targets 450 different banking and financial apps. It’s called Nexus, and it’s an evolution of the mid-2021 SOVA banking trojan. In fact, this botnet was discovered a year ago.
It turns out that this Android banking Trojan is a common tool that many bad actors can use. That is, bad actors who do not have their own MaaS (malware as a service) can get their hands on Nexus and make money with it. According to Cleafy, anyone any hacker can use it to perform account takeover (ATO) attacks for a monthly fee of $3,000.
How does this Android banking trojan work?
The Android Banking Trojan invades your Android system by posing as a legitimate application. However, once it’s in the system, the victim’s device becomes part of the botnet controlled by the hacker.
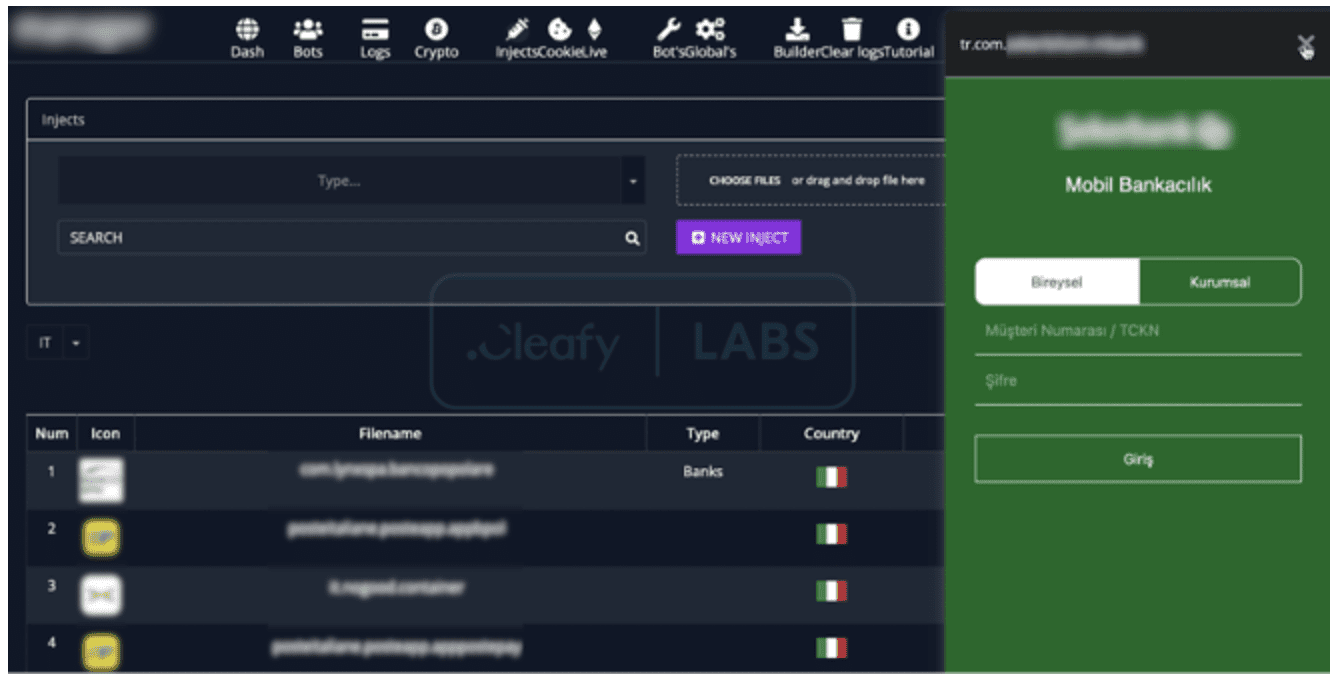
Like other keyloggers, Nexus can record your login credentials in various apps. We know what you are thinking – two-factor authentication (2FA). But this is not the case when it can help you protect your bank accounts. The thing is that Nexus can steal 2FA codes and information sent via SMS from the Google Authenticator application. What’s worse, you won’t know about it because the Trojan will delete 2FA SMS after stealing the codes.
Once the victim’s device becomes part of the botnet, the hacker can remotely monitor it via a web panel and even make adjustments. Currently, it can steal banking credentials from 450 banking applications.
SOVA evaluated
A few years ago, there was a similar MaaS called SOVA. However, its source code was stolen by an Android botnet operator. Nexus was built on the core of SOVA and the stolen code. However, those who created Nexus also added “dangerous elements such as a ransomware module that can lock you out of your device with AES encryption.”

Good news for those in the following countries: Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Uzbekistan, Ukraine, and Indonesia. This Android banking Trojan won’t work on devices in the above countries (lucky me). Most of these countries are the Commonwealth of Independent States (CIS) members.
Hard to discover
This is Trojan malware. So it’s not easy to detect in Android. But if you notice any strange behavior from your smartphone, such as abnormal battery drain or abnormal spikes in mobile data and Wi-Fi usage, it’s better to perform a factory reset on your Android phone.
Another recommendation is to download apps from reputable sources such as the Google Play Store. You should also make sure that your phone is running the latest available security patch and that you only grant apps the permissions they need to run.
So far, there is no information on how widespread the Nexus botnet is. But that shouldn’t make you sit still.





