Two-step authentication is an additional protection system that we use to connect to a service. But, it was bypassed by a group of Chinese hackers nicknamed APT20. Government services and industrial companies, distributed in ten countries are concerned.
Today we have some disturbing news. A group of hackers of Chinese origin would have managed to circumvent the famous two-step authentication, Which is a protection system used by the vast majority of services on the Internet, Google for example, but also (and above all) banking institutions. The information was releasedby a Dutch security specialist, Fox-IT.
Chinese hackers caught bypassing 2FA
Two-step authentication is a standard protection system today and you are certainly using it, even if you don’t know it. It comes in addition to the classic login/password duo. When you enter your credentials on a service using this protection, the latter sends a temporary code that we enter on our device (in the case of Google, the system returns you to your smartphone where you must press a button to confirm that this is not a stranger who is trying to log into your account). By entering the code, you confirm your identity to the system.
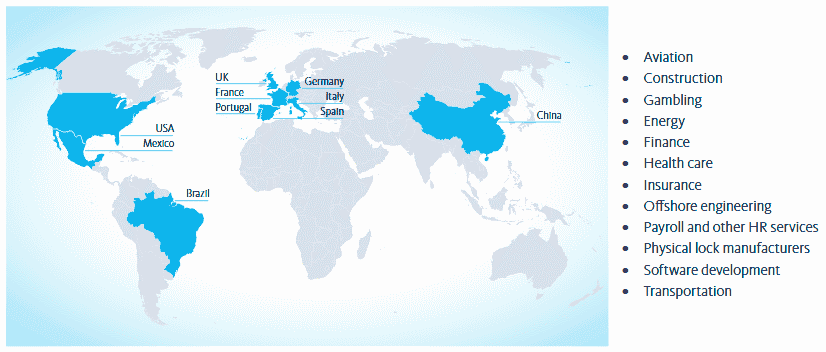
By managing to bypass this authentication, hackers were able to break into certain government departments or servers of industrial companies. One of the victims of these attacks contacted Fox-IT who discovered a suspicious activity. And was able to trace back to the group of hackers mentioned above. The companies affected by hackers are spread across ten countries. And a dozen different industrial sectors.
The list of the countries concerned include France, Italy, Spain, Portugal, Germany, the United Kingdom, Brazil, the United States, Mexico and even China. The sectors in question are aeronautics, construction, finance, energy, insurance, transport, human resources providers, lock designers and gambling. It does not seem that this wave of attacks concerns the general public, but more companies.
APT20 SEEN BYPASSING 2FA
Fox-IT analysts said they found evidence that the hackers connected to VPN accounts protected by 2FA. How they did it remains unclear; although, the Fox-IT team has their theory. They said APT20 stole an RSA SecurID software token from a hacked system, which the Chinese actor then used on its computers to generate valid one-time codes and bypass 2FA at will.
Normally, this wouldn’t be possible. To use one of these software tokens, the user would need to connect a physical (hardware) device to their computer. The device and the software token would then generate a valid 2FA code. If the device was missing, the RSA SecureID software would generate an error.






This article is pretty damn useless. What KIND of 2FA? What protocol? 2FA is a methodology, not a specific technology – saying that 2FA is compromised is like saying that deadbolt locks are compromised.
Agreed. 2fa over text is already known to be vulnerable by cell tower spoofing. Is this article talking about that, or are authy and google authenticator compromised? That’d be the big worry.
Trash article just pushing fear mongering. Get better writers.
Not all 2FA is created equal. Even with the same *kind* of 2FA, the implementation methods are different. They probably hacked into *one* service. That’s does not call for mass panic, fear mongering, and acting like the general public is stupid for not being concerned. Also, AFAIK, top-secret government databases are on a closed intranet. It would be stupid to put that stuff online. I’m not sure they have access to much more than the public records (at least in the US) from the web. (Somebody correct me if I’m wrong on that)
Hmmm
This article is incredibly misleading, if you read the source, you will see that the servers were compromised and not 2fa, saying 2fa is compromised doesn’t even make sense.