The Android world is very vast and diverse and this can negatively contribute to its global security. The story we are about to tell you is an example and has as its protagonist MediaTek. It’s a well-known Taiwanese manufacturer of processors for mobile devices.
It is a dangerous vulnerability discovered in MediaTek chips that expose the devices that use it to serious security risks. However, it is curious to know how the vulnerability emerged and how we realized its danger.
MediaTek has, in fact as early as May 2019, had released a patch to fix it. The problem arose when not all smartphone manufacturers have implemented it on their devices. So this exploit was then analyzed and “used” by an XDA member for positive purposes. In particular, the exploit was used to try to acquire root permissions on the Amazon Fire Tablet. He managed to acquire root permissions by exploiting the vulnerability of the MediaTek chip, completely bypassing the unlocking of the bootloader.
Subsequently, the XDA member verified the chip models on which the vulnerability is present, and then shared the list : MT6735, MT6737, MT6738, MT6739, MT6750, MT6753, MT6755, MT6757, MT6758, MT6761, MT6762, MT6763, MT6765, MT6771, MT6779, MT6795, MT6797, MT6799, MT8163, MT8167, MT8173, MT8176, MT8183, MT6580 and MT6595.
MediaTek vulnerability: Why is it so dangerous?
The bootloader unlock on Android devices is a critical operation in terms of safety. The boot loader enables signature verification into the boot of the operating system. This makes it possible to apply and comply with the security model structured by Google. Once the bootloader is unlocked, it is possible to acquire root permissions. This operation opens the doors to modding possibilities, but also to potential risks. With root access, in fact, particular access permissions to personal information, such as that for the internal archive, do not make much sense to exist because access is still guaranteed to the user with root access.
According to the details shared by MediaTek on the vulnerability, which you can observe in detail through the image below, it can be used on the Linux kernel versions 3.18, 4.4, 4.9 and 4.14 with the Android versions Nougat, Oreo and Pie.
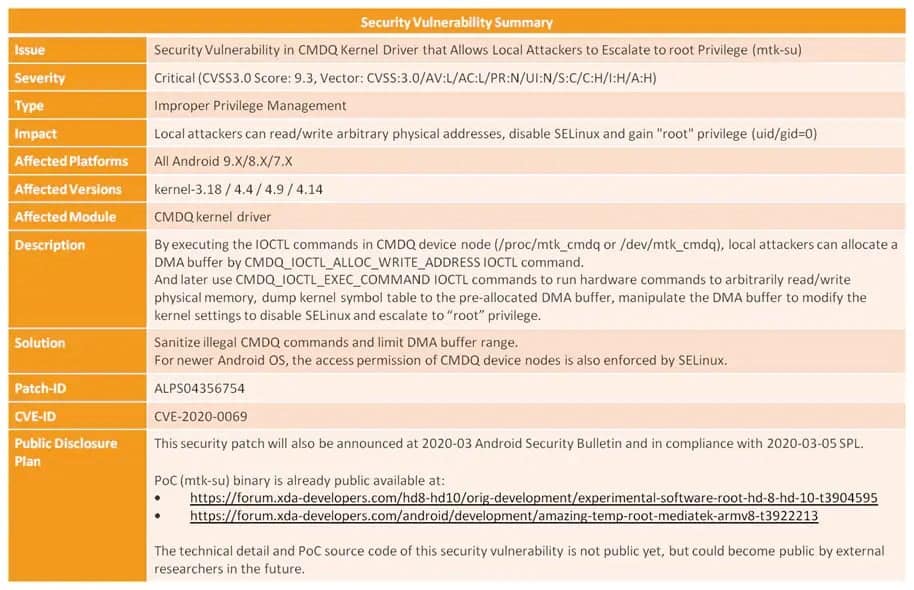
MediaTek has released the software fix to the vulnerability since May 2019 and Amazon was one of the manufacturers that immediately implemented it. Unfortunately, however, to date, March 2020, many manufacturers have not yet implemented it for their devices. MediaTek, unlike Google, cannot even force smartphone manufacturers to implement the software patch.
Google itself is aware of the seriousness of the situation and has asked XDA, which took notice of the situation last month, not to publish it to date to prevent MediaTek from a bad light. Now the vulnerability has been included in the March 2020 Android Security update. This will speed up the adoption of the patch by the affected manufacturers.
How to check if your device is affected?
To check if your device SoC MediaTek is suffering from this critical vulnerability, just manually run the script published in this thread of the XDA forum. If you get access to the shell of the root, this means that your device can be exploited. And therefore you will have to hope that the fix will arrive soon from the manufacturer. Once the device receives the Android security patches of March 2020 it will most likely be protected from the vulnerability.






As Mediatek cpu’s are used in maybe hundreds of Asian mobile phone manufacturers, how are these phone owners going to know if their phones are safe to use for Internet banking, etc?
Yes, rooting your phone ALWAYS involves using an exploit.. I’m yet to hear the dangerous part though…