Linux has been known for being way more secure than Windows PCs. However, this may be changing soon as the platform is growing in popularity. According to a new report from Cybersecurity researchers from Qualys (via TechRadar), there is an “extremely severe” vulnerability in Linux. It’s very easy to exploit bugs and is affecting every major distro for the open-source Operating System.
According to the researchers, this vulnerability has been “hiding in plain sight” for more than 12 years, and it’s memory corruption in polkit’s pkexec. According to the researchers, it’s a SUID-root program, installed by default. The malicious actors can exploit the bug to gain full root privileges on the target machine, and then do as they please. They can use the exploit to install malware or even ransomware.
This exploit has been around for almost a decade
According to Bharat Jogi, Director, Vulnerability and Threat Research department at Qualys, states that this vulnerability is there for almost a decade. Jogi explains Polkit as a component that controls system-wide privileges in Unix-like operating systems, and as such, provides an organized way for non-privileged processes to communicate with privileged ones. One can also use the Polkit to execute commands with elevated privileges. When using the command pkexec, followed by whatever command, it will require root permission.
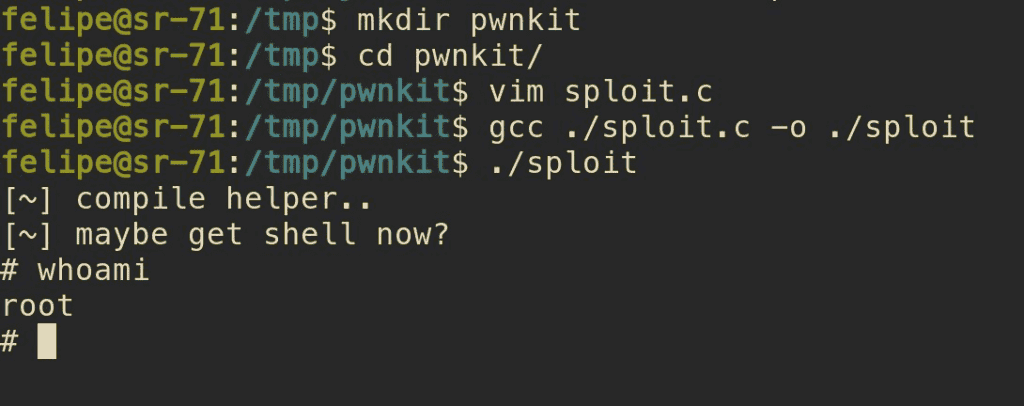
The researchers clearly state that this is an easily exploitable flaw. They’ve tested it on Ubuntu, Debian, Fedora, and CentOS. Other Linux distros such as Linux Mint, ElementaryOS, and so on are “likely vulnerable and probably exploitable”. Qualy states that users should patch up their systems immediately. They need to search the vulnerability knowledgebase for CVE-2021-4034, to identify all the QIDs, and vulnerable asses. Worth noting that the patches are already out for both. So you’re an active and experimental Linux user, you should patch the system immediately.
ZDNet’s Steven Vaughan, states that users whose systems cannot be immediately patched need to remove the SUID-bit from pkexec. It’s a temporary way to get the system secure and free from possible exploitation. According to the developer, this root-powered shell command can stop possible attacks. You can copy the code, press CTRL + SHIFT + T to open the terminal, and paste the above command.
# chmod 0755 /usr/bin/pkexec
Worth noting that around a year ago, Qualys discovered a privilege escalation vulnerability in one of the core utilities present in Unix-like OS including Linux. If exploited, the heap overflow vulnerability in the Sudo utility could allow an unprivileged user to gain root privileges. Therefore, we assume that other vulnerability issues are still going off-radar.





