A new malware called ShadowVault (SV) has been discovered that can steal sensitive info from macOS devices. According to Guardz Cyber Intelligence Research (CIR), the new malware is a macOS – specific threat. CIR claims that it used “sophisticated covert operations” to spot SV while it was in development. Apple Insider and India Today claim that after an SV attack, users’ info such as bank info, crypto wallets, and login details are at risk. Apple Insider also reveals that malware works in the background and can access personal data without the user’s knowledge. In this article, we will discuss the SV malware in detail, including its impact, how it works, and how to stay safe.
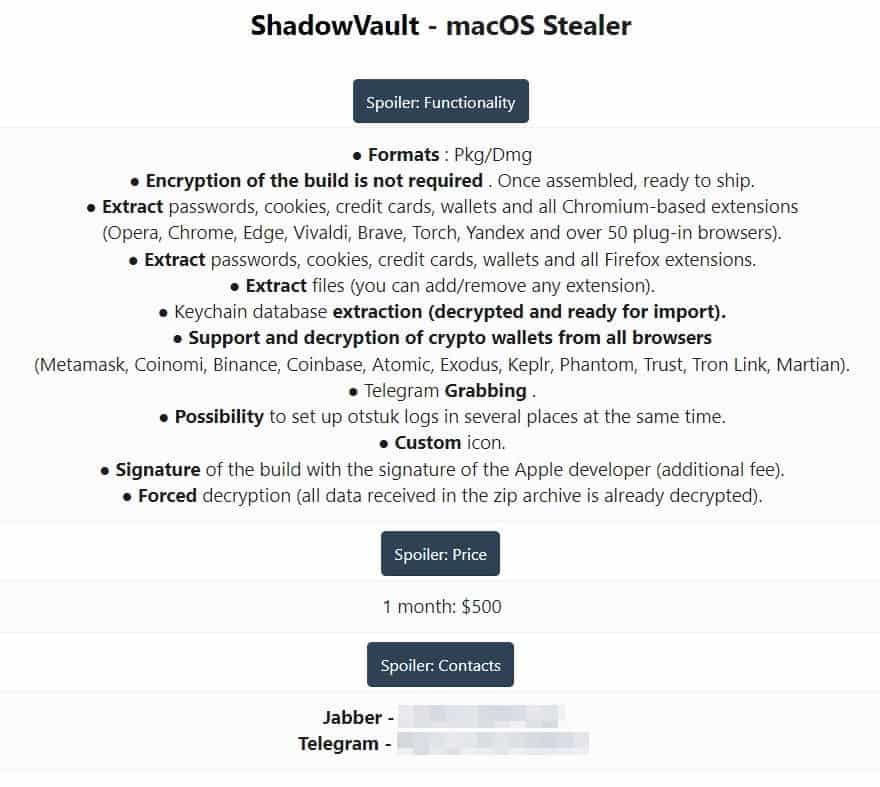
How ShadowVault (SV) malware works
The SV malware works by running in the background on macOS devices and accessing personal data without the user’s knowledge. India Today claims that the malware is typically spread through phishing emails, fake software updates, and other social engineering tactics. Once the malware is installed on the device, it can run in the background and access personal data without the user’s knowledge.
Impact of ShadowVault malware
The SV malware can steal sensitive info from macOS devices without the user having any idea of the theft. This can lead to cash loss, identity theft, and other serious issues. The malware can also weaken the safety of the device and make it exposed to other attacks. Falling victim to the SV malware can have serious impacts. Some of the impacts include
1. Financial or cash loss:
The malware can steal sensitive info such as bank info, credit card details, and crypto wallets, which can lead to cash loss. Most of these malware are designed for cash gains so we must guard against them.
2. Identity theft:
The malware can steal personal info such as login credentials, which can be used to steal the victim’s identity. When a user’s identity is stolen, it can be used to commit a crime and the user will be held even though they know nothing about it.
3. Compromised security:
The malware can weaken the security of the device and make it exposed to other attacks. If this happens, all other data or info in the user’s device is at risk.
4. Unwanted browser redirects:
The malware can cause unwanted browser redirects, changes to the homepage, and other unwanted changes to the device. When you spot such redirects, then it’s time to scan and fix your system.
5. Loss of privacy:
The malware can access personal data without the user’s knowledge, leading to a loss of privacy.

How to stay safe from ShadowVault malware
To protect sensitive data from the SV malware, businesses can take the following measures:
Gizchina News of the week
1. Employee education and awareness:
Train staff on cybersecurity best practices, such as spotting phishing emails, and avoiding suspicious downloads. Also, all staff must make use of only a very strong password. In other words, teach all staff about good password hygiene. From time to time, remind all staff to be cautious and vigilant when handling sensitive data.
2. Use trusted anti – virus software:
Install and regularly update trusted anti – virus software on all macOS devices. This software can detect and remove malware, including the SV malware, and provide real – time protection against new threats.
3. Keep software up to date:
Ensure that all software, including OS and apps, is up to date with the latest security patches. Regularly check for updates and apply them promptly to protect against known vulnerabilities that malware like SV may exploit.
4. Use only strong access controls:
Use strong authentication methods, such as two – factor authentication (2FA) or multi – factor authentication (MFA). This will add an extra layer of security to sensitive data. Also, limit access to sensitive data only to authorized personnel and regularly review and update user access privileges.
5. Regular data backups:
Implement a regular data backup strategy to ensure that critical data is securely stored and can be restored in case of a malware attack or data loss. Store backups in a separate location or on a cloud-based platform with strong security measures.
6. Network segmentation and monitoring:
Implement network segmentation to isolate sensitive data from other parts of the network. Monitor network traffic and implement intrusion detection and prevention systems (IDPS) to detect and block any suspicious activity.
7. Incident response plan:
Develop and regularly update an incident response plan that outlines the steps to be taken in the event of a malware attack. This plan should include procedures for isolating infected devices, notifying relevant stakeholders, and restoring systems from backups.
8. Regular security audits:
Conduct regular security audits to identify vulnerabilities and weaknesses in the IT infrastructure. This can help identify potential entry points for malware and allow for timely remediation.
In summary, to avoid SV attacks, users have to be very careful when opening emails, mostly emails from sources they do not know. For downloads, make sure they are from sources that you trust such as the official app stores. All passwords should be very strong and antiviruses should be from trusted brands.
By using these tips, brands can to a large extent reduce the risk of falling victim to the SV malware. Also, they will protect their sensitive data from unauthorized access and theft.

Final Words
The SV malware is a serious threat to macOS devices, as it can steal sensitive info such as bank info, crypto wallets, and login details. To stay safe from this malware, it is important to keep your device up to date with the latest security updates. Also, be careful when opening emails from unknown senders and only download software updates from trusted sources. In addition, use very strong and unique passwords as well as reputable antivirus software to scan your device for malware and other security threats. By taking these precautions, you can protect yourself from SV malware and other similar threats.





