Security researcher Jonas Lykkegaard discovered a vulnerability in the Windows operating system that allows a low-level user to gain administrator rights on a local computer. According to reports, the issue affects Windows 10 and Windows 11.
In the course of the research, they found that even without administrator rights, a Windows user can access confidential files of the registry database in order to independently increase the level of privileges in the system. The Windows Registry acts as a kind of configuration repository for the operating system; and contains hashed passwords, user settings; and configuration settings for applications alongside decryption keys, and much more.
At the same time, the database files associate with the registry are available in the C: \ Windows \ system32 \ config folder. These are the SYSTEM, SECURITY, SAM, DEFAULT and SOFTWARE files. Because these files contain confidential information about all device user accounts and security tokens used by Windows features; normal users should not get access to them. This is especially true for the Security Accounts Manager (SAM) file; as it stores the hashed passwords of all users on the system.
Gizchina News of the week
A vulnerability in Windows 10 and 11 allows anyone to gain administrator rights
Through research, Lykkegaard found that Windows 10 and Windows 11 SAM-related registry files, as well as other registry databases, are available to users of the device with low privileges. This means that an attacker, even without administrator rights, can extract the hashed NTLM passwords for all accounts on the device and use them in hash-passing attacks to elevate privileges. Despite the fact that files like SAM are always in use by the system and an attempt to access them will be denied, the system creates hidden copies of them, which are used by the attacker in this type of attack.
According to available data, users with normal privileges were able to access the files for the first time in Windows 10 (1809). Microsoft has confirmed the problem, and the vulnerability is being tracked under the identifier CVE-2021-36934. The developers also proposed a temporary option to change the access settings; which will avoid potential troubles associated with this vulnerability. “We are investigating the situation and, if necessary, will take appropriate measures to protect customers;” a Microsoft spokesman commented on the issue.
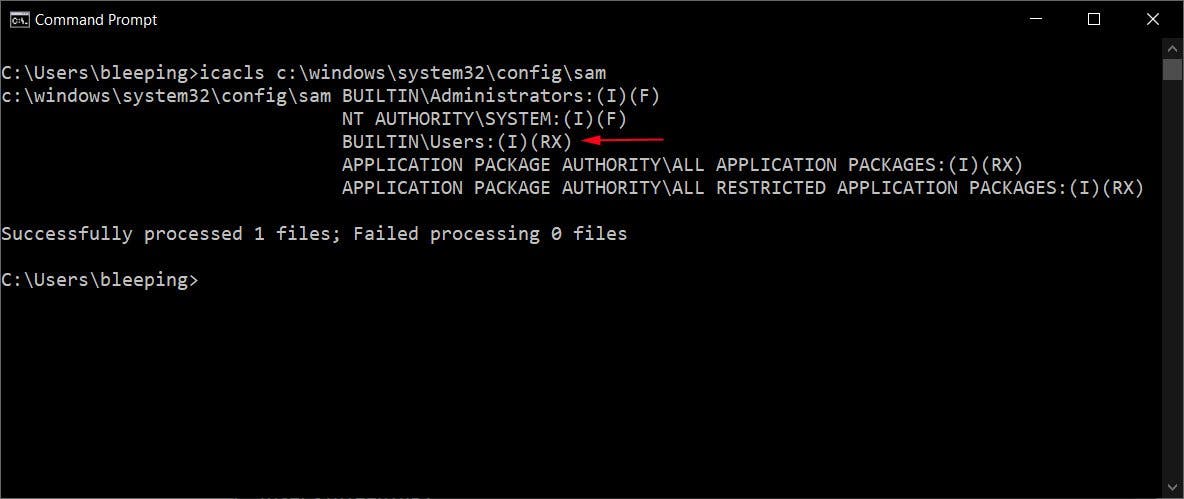
To block exploitation of this vulnerability temporarily you need to take the following steps:
Restrict access to the contents of %windir%\system32\config:
- Open Command Prompt or Windows PowerShell as an administrator.
- Run this command:
icacls %windir%\system32\config\*.* /inheritance:e
Delete Volume Shadow Copy Service (VSS) shadow copies:
- Delete any System Restore points and Shadow volumes that existed prior to restricting access to %windir%\system32\config.
- Create a new System Restore point (if desired).




