Hackers Use Trusted Apple Certificates to Hide New Mac Malware
AppleWednesday, 31 December 2025 at 07:35

For years, a lot of people figured Macs
were just safer than PCs. It wasn't necessarily because Apple was perfect. It was mostly because hackers spent all their time picking on Windows users. But now
that Macs are everywhere, the bad guys are starting to pay much closer
attention.

A new report from Jamf Threat Labs just found a sneaky type of virus. It's really good at pretending to be a normal, safe program. It’s a wake-up
call that as these devices get more popular, they’re becoming bigger targets
for much smarter attacks.
Read also
Stealing Trust to Bypass Security
The most alarming part
of this discovery is how the hackers bypass Apple’s security checks. Normally, apps downloaded outside the official store need a
digital "stamp of approval" called a Developer ID certificate.
Hackers are now buying or stealing these real certificates from underground
markets. Because the malware is signed with a genuine Apple ID, it looks
perfectly legal to the operating system. This allows the malicious software to
skip past the standard warnings that usually stop unverified apps from running.
A Clever Bait and Switch
The hackers are also
using a smart trick to get past Apple’s automated reviews. When they submit
their code for approval, they send a "clean" version that does
nothing wrong. This harmless shell is written in Swift, a common language for Mac
apps. Once a user installs the program, the app waits until it is safely
on the computer before connecting to a remote server. Only then does it
download the actual virus. By keeping the bad code in the cloud until the last
second, the hackers make it almost impossible for initial scans to catch them.

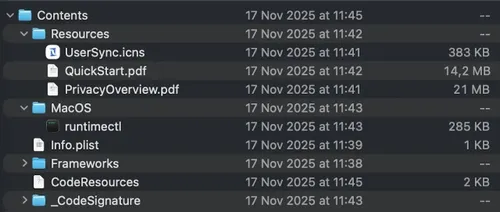
New Methods of Infection
This specific
threat is a new version of the MacSync Stealer. In the past, this virus tried
to trick users into typing complicated commands into their computers. The new
version is much stealthier and more automated. It arrives hidden inside a fake
software installer that looks like a standard messaging app. Once you open it, a hidden script runs in the background without any
warning. It even includes "decoy" files, like fake PDFs, to make the
file size look normal and stay under the radar of security tools.
Avoiding Detection and Apple’s Response
The people behind this malware added
several tricks to keep it hidden. The program makes sure you're online and even
uses a timer so it doesn't run too often and get noticed. This prevents the computer from slowing down, which might
tip off the user that something is wrong. While some security programs missed
the threat entirely, Jamf was able to track it down. They reported the stolen IDs to
Apple, which has since cancelled the certificates to stop the virus from
spreading further.
Popular News
Latest News
Loading




